6. Configuration
Aurora uses the YAML format for its configuration file. All values set in the config file can also be used as command line flags.
There are two modes of operation:
Aurora started directly from the command line, optionally using a config passed with the
--config/-cflagAurora started as a service (see chapter Installation) for more details) with a config file located in
C:\Program Files\Aurora-Agent\agent-config.yml
6.1. Configuration Presets
To facilitate the use of Aurora, four configuration files are part of the Aurora package:
Standard (
agent-config-standard.yml)Reduced (
agent-config-reduced.yml)Minimal (
agent-config-minimal.yml)Intense (
agent-config-intense.yml)
An installation that uses the preset named "reduced" would look like this:
C:\aurora>aurora-agent.exe --install -c agent-config-reduced.yml
The configuration presets effect the following settings:
Affected Setting |
Minimal |
Reduced |
Standard |
Intense |
|---|---|---|---|---|
Deactivated Sources |
Registry, Raw Disk Access, Kernel Handles, Create Remote Thread, Process Access, Image Loads |
Registry, Raw Disk Access, Kernel Handles, Create Remote Thread, Process Access |
Registry, Raw Disk Access, Kernel Handles, Create Remote Thread |
|
CPU Limit |
20 % |
30 % |
35 % |
100 % |
Process Priority |
Low |
Normal |
Normal |
Normal |
Minimum Reporting Level |
High |
High |
Medium |
Low |
Deactivated Modules |
LSASS Dump Detector, BeaconHunter |
LSASS Dump Detector |
Warning
Intense preset uses the most system resources and can put the system under heavy load, especially if a process accesses many registry keys in a short amount of time.
We recommend using this preset only on a very selective set of systems or in cases in which maximum detection is required.
6.1.1. Custom Profiles
If you need a more specialized configuration than these predefined ones, you can also create your own configuration for maximal adaptability.
6.2. Output Options
The following output options are available
Windows Eventlog (default)
Log file
UDP target
TCP target
Output is usually formatted in a human readable way (with KEY: value pairs).
For machine ingestion, using --json is recommended, which changes the format to JSON structs.
6.2.1. ASGARD Analysis Cockpit
Whenever you install an ASGARD Agent, the controlled Aurora Agent Services gets its configuration automatically. In a default setup, all logs generated by an Aurora Agent will be relayed via an ASGARD to an Analysis Cockpit system.
6.2.2. Windows Eventlog
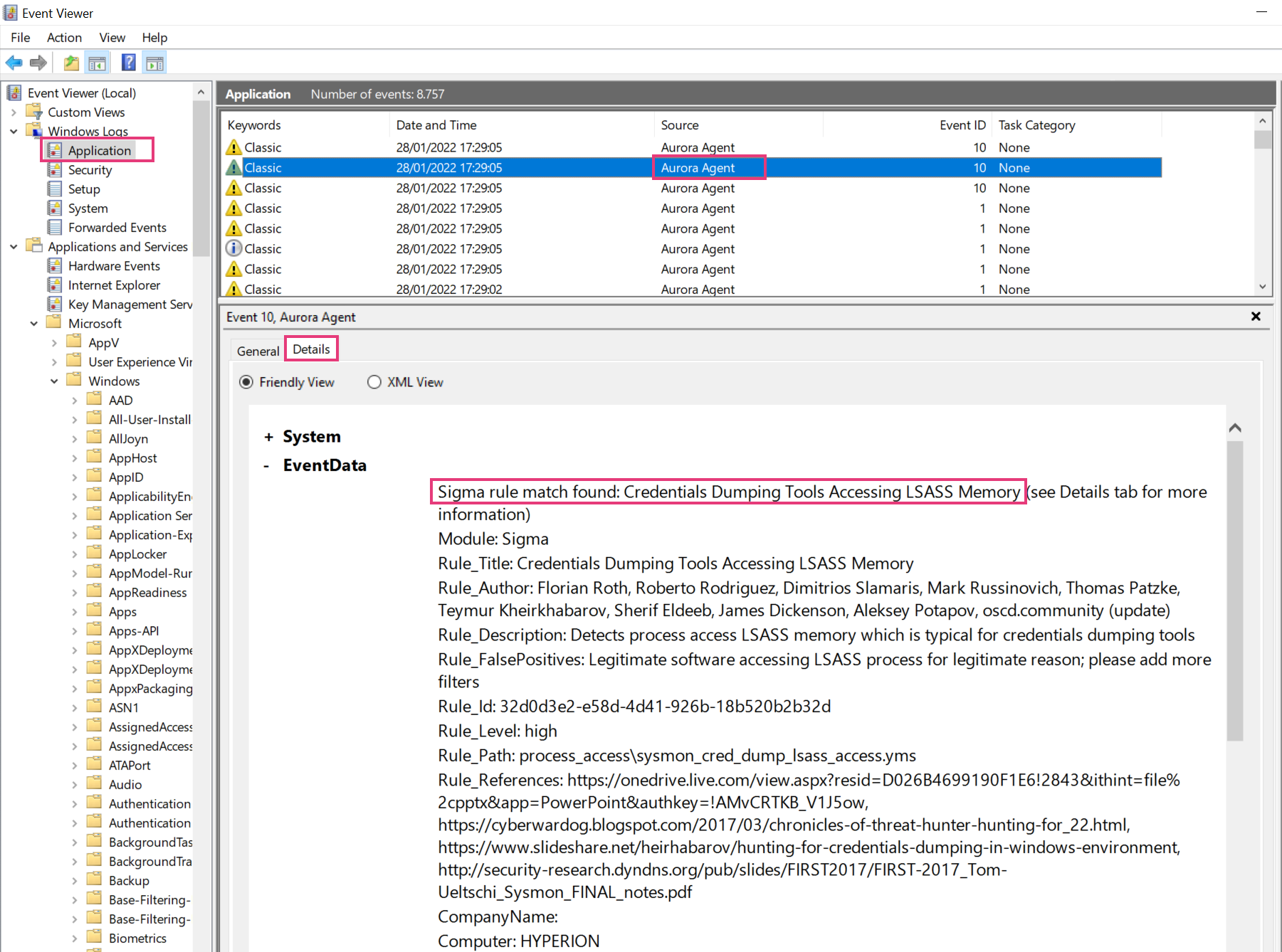
By default Aurora writes its event into the Windows event log "Application". To review the events use the Windows "EventViewer". Make sure to check the "Details" tab to see all fields and values.
6.2.3. UDP / TCP Targets
UDP or TCP log targets can be specified via the --udp-target and --tcp-target
options. These options take an argument in the form host:port, e.g. myloggingsystem.internal:8443.
6.2.4. Log File
A log file can be specified using --logfile. By default, no log file is written.
The log file is automatically rotated by Aurora once more than --log-size bytes have been written to it (default is 10MB).
--log-rotate can be used to specify the number of log rotations that are retained (defaults to 7).
Log rotation can be disabled by setting --log-size to 0.
6.3. Process Exclusions
To exclude specific processes from analysis, you can configure Aurora to ignore all events from specific image paths.
In order to do so, the excluded images must be specified (as regular expressions) in a file that is passed to --process-excludes.
By default, config\process-excludes.cfg is used. This file contains further examples on how to specify the
excludes.
The Process Exclusions are typically the values in your PARENTIMAGE field (Process Creation Event) or IMAGE (for all
other Events - File Creation, etc.).
Adding the expressions in the file results in
Lower CPU load caused by the exclusion of the process
No more matches on events generated by the excluded process
The process exclusion file is loaded at startup. If you change the file, you'll need to restart Aurora to apply those changes.
Hint
Please be aware that adding process exclusions can cause malware that uses process hollowing or similar techniques to mask themselves as an excluded process to go unreported.
6.3.1. Exclusion Examples
To get get a full list of high volume event sources, use the following command:
aurora-agent-64.exe --status --trace
...
By process:
866420 events from C:\Program Files (x86)\NoisyService\serv.exe
66420 events from C:\Windows\System32\svchost.exe
11369 events from C:\Program Files\Microsoft VS Code\Code.exe
You identify the first entry in the list as the top speaker that you'd like to exclude from the observation. Accordingly, the exclusion should look like this:
C:\\Program Files \(x86\)\\NoisyService\\serv\.exe
The expressions are applied:
as contains, so there is no need to add
.*at the beginning or the end of itcase-sensitive
Make sure that escape every character that has a meaning in regular expressions.
6.4. False Positive Filtering
When encountering false positives or known anomalies, besides reporting them,
you can also exclude them using a false positive filter file.
By default, config\false-positives.cfg is used.
The file passed should contain a regular expression per line; any log lines where any of these false positive regexps matches will not be logged.
If you want to exclude all events from a specific process, process exclusions might be a better choice than a false positive filter since they also cancel any analysis on those events; see Process Exclusions for more details.